What is LoRaWAN?
Quoting from the LoRa Alliance,
“The LoRaWAN® specification is a Low Power, Wide Area (LPWA) networking protocol designed to wirelessly connect battery operated ‘things’ to the internet in regional, national or global networks, and targets key Internet of Things (IoT) requirements such as bi-directional communication, end-to-end security, mobility and localization services.”
LoRaWAN, which stands for Long-Range Wide Area Network, is one of the most commonly used network technologies for IoT devices with a wide range area of deployment.
LoRaWAN belongs to the LP-WAN (Low Power WAN) technology, which by its name, uses a low power -- which means its device could last for 10+ years of operation -- to provide communications between different devices in a long distance to each other.
How Does LoRaWAN Work?
LoRaWAN technology implements a star-on-star architecture, with a gateway as its access point. The technology communicates by CSS (Chirp Spread Spectrum) modulation, which enables the transmission of data within a wide band of increasing and decreasing frequencies. This method of modulation increases the security of the data being transferred, along with the AES-128 encryption provided.
The security of data transferred across the network can still be adjusted based on your choice of data transfer protocol. LoRaWAN has not had any predefined protocol yet, so the protocols to be chosen can be absolutely up to you, considering also the different security architectures that each data transfer protocol provides.
When compared with the other LP-WAN technologies, like NB-IoT, LoRaWAN has a lower operating current, hence a longer battery life. The range covered by LoRaWAN is greater than NB-IoT too -- LoRaWAN could reach up to 20 km in rural areas, but NB-IoT could only reach 10 km. Despite this, NB-IoT would not require any additional gateways for its operation, but LoRaWAN still requires gateways.
Modulation Technique
As was previously stated, the LoRaWAN technology enables communication through Chirp Spread Spectrum modulation.
The proprietary spread spectrum modulation technology is a signal transmitting technique done by distributing the signal across a wide band of frequencies and for a low power density. The technique is the reverse of the narrowband technique (enable narrow frequency band and high power density) which is used by the NB-IoT technology.
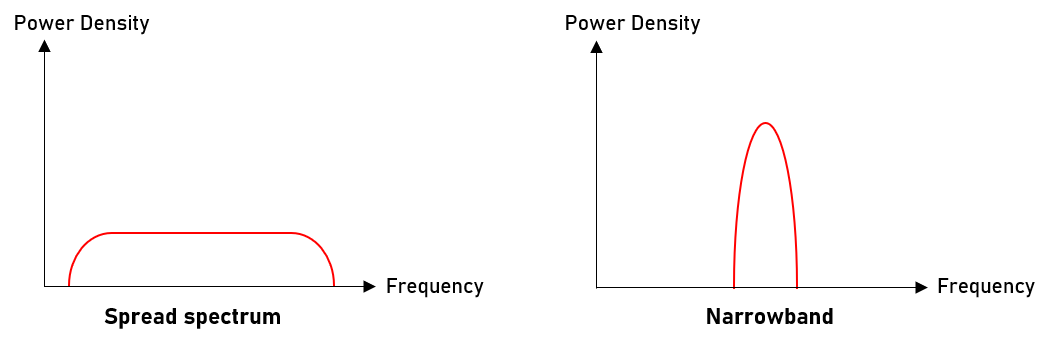
Since the spread spectrum technique uses a wide band of frequency for signal deliveries, the communication established are resistant to tampering or interference.
Chirp Spread Spectrum (CSS) is one type of the spread spectrum technique. Other branches include the Frequency-hopping Spread Spectrum (FHSS), Time-hopping Spread Spectrum (THSS), and Direct-sequence Spread Spectrum (DSSS).
The chirp spread spectrum technique works by increasing or decreasing the frequency of the transmitted signal over time. These signals are to be distinguished from one another by its starting or initial frequency. An advantage of this CSS technology is that it's resistant to the Doppler Effect which might occur to other delivering signals and noises.
LoRaWAN's CSS technology also allows the multicast function, which occurs when the system server transmits data to numerous end nodes at the same time, and vice versa: the server is able to accept numerous data from its end nodes at the same time.
Device Operation Types
LoRaWAN is developed under the LoRa Alliance, which is an international non-profit association dedicated to standardizing the LoRa technology. This means all devices which claim to be able to support LoRaWAN technology must first pass the standard testing by the LoRa Alliance.
As one of the initial founding members of the LoRa Alliance, the company Semtech has been the main manufacturer for LoRa transceivers. Transceivers, by definition, are the component which assists the transmitting and receiving of communication signals. These will be implemented in the gateways and end-nodes, to enable communication between different devices.
LoRa itself has 3 types of transceiver operations, Class A, Class B, and Class C. Different transceivers each has different supporting capabilities, but the default operating condition would be the Class A Operation.
The Class A operation enables the lowest power consumption, but with the cost of the highest deterministic downlink latency time when compared with the other operating classes. As you go down the class from Class A to C, the power consumption gets higher and the downlink latency gets lower. This being said, the Class C operation is only supported by devices which run on mains power.
Security
LoRaWAN's physical layer, LoRa, implements the AES (Advanced Encryption Standard) system for its security protocol, using its 128-bit encryption capability. According to the U.S. government’s NSA (National Security Agency), the AES-128 algorithm is sufficient to protect classified information up to the SECRET level, or MEDIUM Security.
The AES system has 3 types of operation: 256 bits, 192 bits, and 128 bits.
The AES-128 architecture is also used within the IEEE 802.15.4 standard, which is specified for WPANs. The algorithm of how AES works implements a XOR type encryption in its first stage. To first establish a connection for data transmission, the system will enable a symmetric pair for encryption to take place.
A symmetric pair is a set of public keys, in which is only obtained by the transmitting and receiving devices. The keys are the same for both side, and is unique to the system. Hence when the encryption process occurs, only the corresponding devices were able to access the information. This hence prevents tampering to occur during the delivery.
Other than the symmetric public key pair, the architecture also implements several types of session keys. These session keys are used to ensure connections between the transmitting and receiving devices are maintained throughout the communication process. The architecture itself implements several types of session keys:
- AppSKey (Application Session Key)
The AppSKey is generated to encrypt and decrypt the data for transmission between the end node and the server.
- NwkSKey (Network Session Key)
The NwkSKey is generated to ensure the integrity of the transmitted data, by validating the MIC (Message Integrity Code). This was done under the AES-CMAC feature of the AES system.
LoRaWAN vs Other Technologies
As the number of IoT deployments increase, different methods of connecting different devices have been established. The two main IoT network deployments are short-range networks, such as BLE (Bluetooth Low Energy), Zigbee, and Z-wave, or long-range networks, which include the LPWANs.
Amidst the vast development and exponential growth of IoT and M2M connections established, the LPWAN has in particular had been getting a lot of attention due to its stable and long-term ability for remote monitoring and controlling.
There are several commonly used network types for LPWAN deployment: LoRaWAN, NB-IoT, Sigfox, and Ingenu. The difference between these 4 types of networks are further discussed below.
| LoRaWAN | NB-IoT | Sigfox | Ingenu | |
| Bandwidth | 125, 250, 500 kHz | 200 kHz | 100 Hz | 0.5, 1, 12 MHz |
| Range | 5 km (urban), 20 km (rural) | 1 km (urban), 10 km (rural) | 10 km (urban), 40 km (rural) | 15 km (urban), 500 km line LOS |
| Power | Very low | Low | Very low | Low |
| Data rate | 0.3 to 50 kbps | up to 200 kbps | 100 bps | 78 kbps |
| Modulation | CSS | QPSK | BPSK | RPMA technology |
| Frequency | Unlicensed ISM bands | Licensed LTE frequency bands | Unlicensed ISM bands | 2.4 GHz |
| Battery Life | up to 20 years | up to 10 years | up to 15 years | 20+ years |
| Security | AES-128 | LTE Encryption | Sigfox systematic protection | Remove IP devices, use REST API |
| Standard | LoRa Alliance | 3GPP | Sigfox company | |
| Topology | Star of stars | Star | Star | Star, tree |
LoRaWAN, when compared with NB-IoT and Sigfox, operates at a generally wider bandwidth, as it uses CSS modulation. The wide bandwidth helps with its noise immunity, preventing interference from stronger signals at a specific frequency.
However, LoRaWAN has a relatively lower data transfer rate in comparison with the other technologies (except for Sigfox). This was done to compensate for the low power operation of the LoRaWAN. With this, the LoRa Alliance claims that LoRaWAN devices can typically run continuously for up to 20 years.
How To Setup A LoRaWAN Network
To set up a LoRa network, you'll need 2 types of major components: the end-nodes and the gateways or concentrators. These devices can be obtained either off-the-shelf or you may design them yourself based on your system needs.
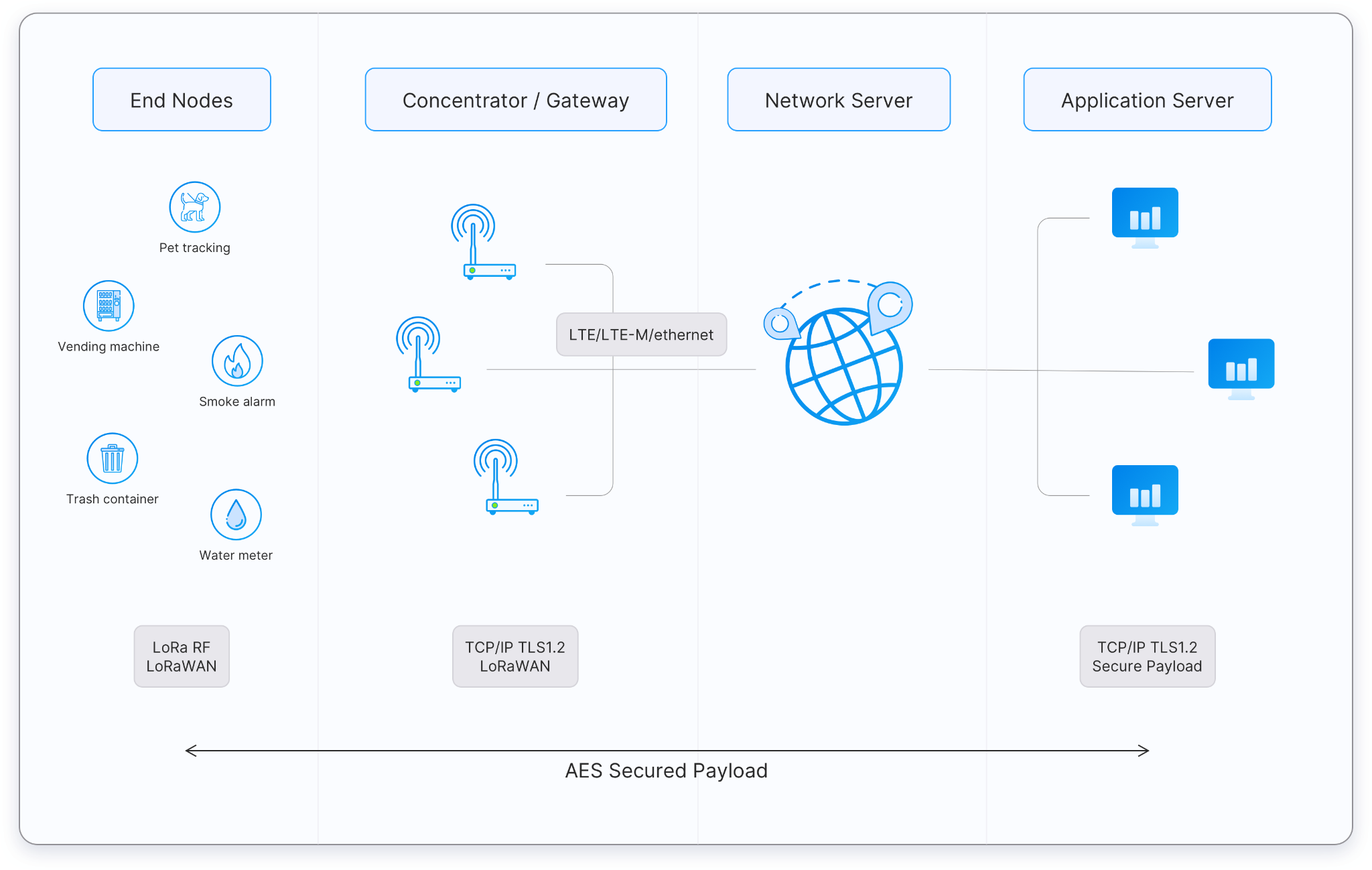
The devices will connect your system to the LoRaWAN server through a backbone, which could be either cellular connections or WiFi. The devices are identified by the IP address. This server will then connects your system devices to the readily available application servers, which allows interaction in the form of software applications. This exchange of data is securely protected using the TLS protocol.
Network Devices
The end-nodes, like its name, are devices at the 'end' of the network. These devices act as the input and/or output to the system. Sensors, monitors, alarms, and buzzers are considered to be the end-node devices when implemented in the network.
Concentrators or commonly known as gateways are the hubs that connect the end-nodes to the LoRaWAN server for communication between devices to occur. The gateway to be set up in your network must first be set up and registered to the LoRaWAN network and must comply with the regulations present in your region.
Alternatively, you can read our LoRaWAN Device Selection Guide with examples of products that you can buy today. Link is down below:
LoRaWAN Regions
Unlike commonly used Local and Personal Area Networks like WiFi and Bluetooth, LoRaWAN doesn't run on the 2.4 GHz license-free band. Instead, it runs in different frequencies based on the unlicensed ISM bands, with specified operating conditions in each region.
These regions, which are based on a set of parameters called ITU regulations, have different operating conditions: frequency bands, data transfer rates, channels, and transfer powers. With different operating conditions, the components used for the devices will also be different.
Hence, different regions require different gateways and end nodes. We provided some example products in the downloadable resource above.
